Blockchain analytics
We are applying blockchain analytics to approach different problems:
- Ransomware payment tracking and characterization.
- Dust analysis and optimization.
- System decentralization measurement.
- Monitoring the adoption of technical updates.
Ransomware payment tracking
Ransomware is a significant threat in today's society, causing disruptions across various sectors, from healthcare to critical infrastructure. Since the early days of cryptocurrencies, illegal actors have leveraged their properties, particularly their decentralization (and censorship resistance), absence of central authorities, and alleged pseudonymity, to facilitate illicit transactions, circumventing financial controls and avoiding detection.
Blockchain transactions form intricate graph structures, and recent progress in Graph Neural Networks (GNNs) has significantly enhanced their ability to model such complex relational data. In our work, we leverage GNNs to detect and characterize ransomware payments within the highly interconnected transactional networks of cryptocurrencies. However, applying GNNs to blockchain analysis presents several challenges. First, the ever-expanding nature of blockchains results in massive and complex graphs that are computationally demanding to process. Moreover, identifying illicit activity such as ransomware payments is extremely difficult due to the rarity of such transactions, leading to limited availability of labeled data. This scarcity underscores the need for effective anomaly detection methods capable of isolating rare malicious behavior from a large volume of legitimate activity. Compounding this issue is the unreliability of existing labeled datasets. Lastly, the constantly evolving tactics of cybercriminals and the tools they employ modify transaction patterns over time, highlighting the importance of adaptive models that can keep pace with these changes.
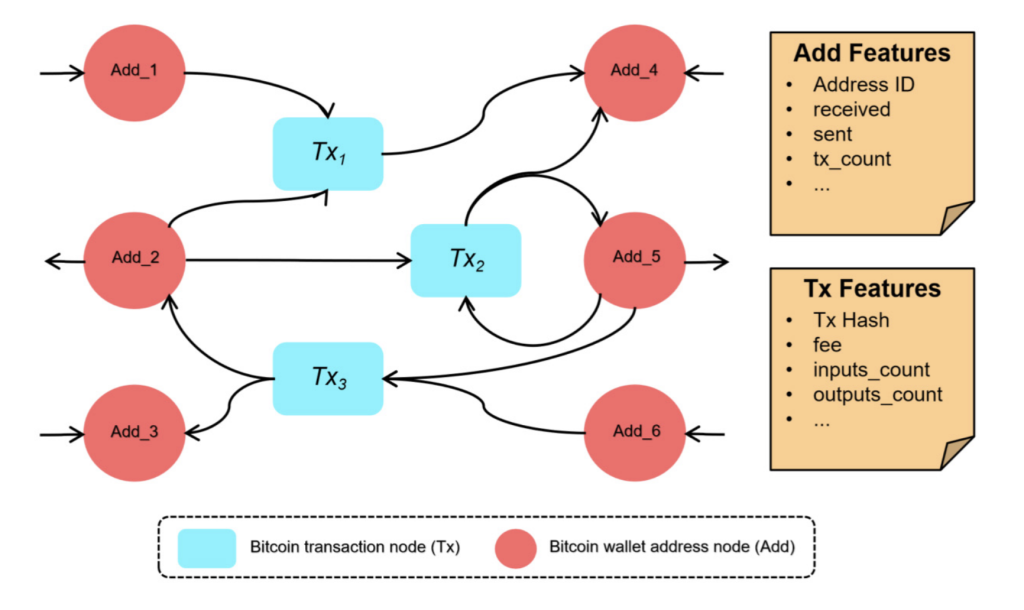
Dust analysis and optimization
Unspent Transaction Outputs (UTXOs) serve as the foundational mechanism for representing coins in many cryptocurrencies. While this model offers several advantages, it also introduces certain complexities that, if not properly addressed, can lead to inefficiencies in the system. These inefficiencies often stem from wallets—software tools that facilitate coin transfers—failing to manage UTXOs effectively during transactions.
In this line of work, we first presented a tool designed to study and analyze the Bitcoin UTXO set, accompanied by a detailed examination of its format and operational characteristics. Our analysis offered a comprehensive overview of the UTXO set and quantified the differences between the two existing formats available to date. Additionally, we provided an in-depth assessment of the volume of dust and economically unviable outputs contained within the set, the distribution of block heights at which outputs were created, and the prevalence of non-standard output types.
We also examined three major UTXO-based cryptocurrencies: Bitcoin, Bitcoin Cash, and Litecoin. These three cryptocurrencies rank as the top UTXO-based networks by market capitalization. Our analysis revealed usage differences among them, resulting in distinct outcomes. Additionally, it highlighted that transaction management has not always been optimal, contributing to a suboptimal state of their UTXO sets.
System decentralization measurement
The Bitcoin Lightning Network (LN) introduces a disruptive approach to payments by enabling fast, scalable, off-chain transactions that operate in parallel with the Bitcoin blockchain, effectively alleviating on-chain congestion. Gaining insight into the LN’s topology is essential—not only for optimizing performance but also for maintaining its security and privacy properties. The structure of the network directly influences payment routing success, robustness to failures and attacks, and the privacy of transactions. While existing research on LN topology primarily focuses on node centrality using metrics such as degree, betweenness, and closeness, these studies often provide a limited view by relying predominantly on channel capacity as the defining characteristic.
Our work makes two key contributions. First, it revisits the application of standard centrality metrics in the context of the LN. Second, it introduces alternative metrics and network features to better capture centrality, including strength, Opsahl centrality, and current-flow betweenness, as well as properties such as capacity, fees, balances, channel types, and pending Hashed Timelock Contracts (HTLCs). Using these expanded metrics, we conduct a comprehensive analysis to identify which measure most effectively captures centrality within the Lightning Network.
Monitoring the adoption of technical updates
Segregated Witness (SegWit) stands out as one of the most controversial upgrades to the Bitcoin protocol to date. Although introduced as a soft fork—meaning it maintained backward compatibility—its deployment faced significant resistance from portions of the Bitcoin community, particularly some miners. This division ultimately culminated in a split of the Bitcoin blockchain, resulting in the creation of a separate cryptocurrency: Bitcoin Cash. The controversy surrounding SegWit was not merely technical but also deeply political, reflecting differing visions for Bitcoin's future, especially in terms of scaling and transaction throughput.
In this work, we presented a detailed overview of the SegWit upgrade, outlining the motivations behind its introduction and the technical improvements it brought to the Bitcoin network. Specifically, we discussed its role in mitigating transaction malleability, a long-standing vulnerability affecting the security and reliability of the protocol, and in enabling more efficient off-chain scaling solutions such as payment channels. Additionally, we examined the adoption of SegWit within the Bitcoin ecosystem, providing empirical data that reflects its uptake and the extent to which its intended benefits have been realized in practice.