We are currently carrying out an in-depth study on wallet fingerprinting in Bitcoin, aiming to understand how different wallets — both software and hardware — shape transactions and what privacy risks these “fingerprints” pose for users.
The objective
When a user transacts in Bitcoin, their wallet software decides on critical details: input and output ordering, address types, fee strategies, and more. These choices embed subtle patterns, or fingerprints, into transactions, which adversaries can leverage to identify wallets and link transactions together — compromising Bitcoin’s pseudonymity.
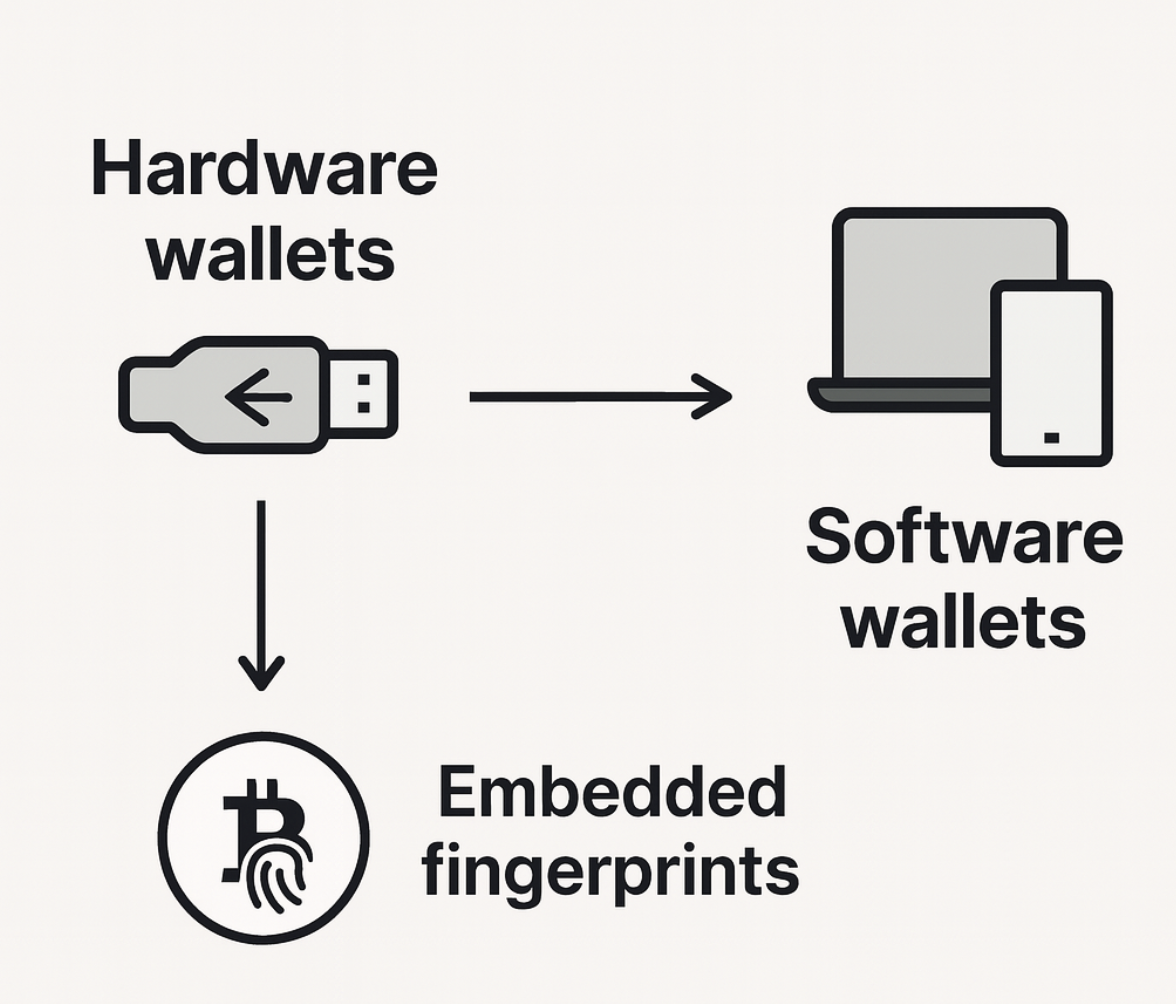
Our study’s goal is to dissect these fingerprints and understand how they originate, separating the influence of software wallets (which build transactions) and hardware wallets (which sign them).
Why is this important?
While Bitcoin is often thought of as private, it is actually pseudonymous. Every transaction is permanently visible on the blockchain. Combined with wallet-level fingerprints, this visibility can become a powerful tool for surveillance and deanonymization.
Previous research, like that of Ishaana Misra, showed that even simple heuristics can already identify about 50% of wallet clients in specific blocks. Our work extends these efforts by adding new heuristics — such as dust output analysis, fee rounding precision, and custom scripting detection — and, for the first time, systematically analyzing hardware wallet signatures.
Our approach
To ensure robust and controlled experiments, we developed Labnet, an isolated Bitcoin network that replicates mainnet behavior but allows unlimited transaction generation without risking real funds or affecting user privacy. If you’d like to learn how to build your own Labnet at home, we shared a detailed guide in our post “Building your own mainnet”.
We tested ten popular hardware wallets (like Trezor, Ledger, Coldcard, and others), finding that they mainly influence signatures rather than broader transaction structure. Software wallets, however, proved to be the main source of distinctive patterns. We studied major wallets including Electrum, Sparrow, Blockstream Green, and Bitcoin Core, identifying over 30 different traits that can act as fingerprints.
A major advance in our recent work has been the automation of wallet user interfaces using Sikuli, a tool that automates screen interactions via image recognition. This allows us to systematically create thousands of transactions with Sparrow, Electrum, and Blockstream Green — adding to the mass transaction generation we had already implemented via RPC for Bitcoin Core.
This massive dataset of labeled transactions (each tagged with its true wallet of origin) will be used to train machine learning models for automated wallet fingerprinting. The goal is to develop a model capable of identifying the wallet that generated a given transaction purely from on-chain data, further quantifying the privacy risks users face today.
We also built an extended Python fingerprinting framework, integrating these new heuristics and supporting a broader range of wallets. In controlled tests, our updated heuristics increased identification accuracy from 18% (with the original code) to 45%.
Results and privacy implications
Our findings show that many modern Bitcoin wallets leak consistent, deterministic patterns that can be exploited to deanonymize users. Even seemingly minor choices — like how fees are rounded or how change outputs are handled — can reveal the wallet used.
This raises significant privacy concerns. Chain analysis firms or malicious actors can potentially cluster transactions, profile users, or even link wallet activity back to identities.
To mitigate these risks, we recommend wallet developers adopt more privacy-preserving defaults: randomizing change output positions, supporting flexible scripting, and ensuring features like opt-in Replace-by-Fee and anti-fee sniping are enabled. Users should avoid address reuse, prefer wallets with strong coin control, and consider diversifying wallets to reduce behavioral correlation.
Interested?
If you’re curious about this topic, want to learn more technical details, or are interested in collaborating — especially around machine learning-based wallet fingerprinting — feel free to reach out at david.corral.urbano@uab.cat.