by Daniel Molina & Jordi Herrera-Joancomartí — November 2025 The challenge of decentralization security When Ethereum transitioned from Proof of Work to Proof of...
When we talk about self-custody and protecting our bitcoins, we understand that the seed used to generate our private keys must be completely isolated...
Introduction Detecting malicious activity in cryptocurrency networks like Bitcoin relies on datasets labeled with licit and illicit transactions. However, these datasets often suffer from...
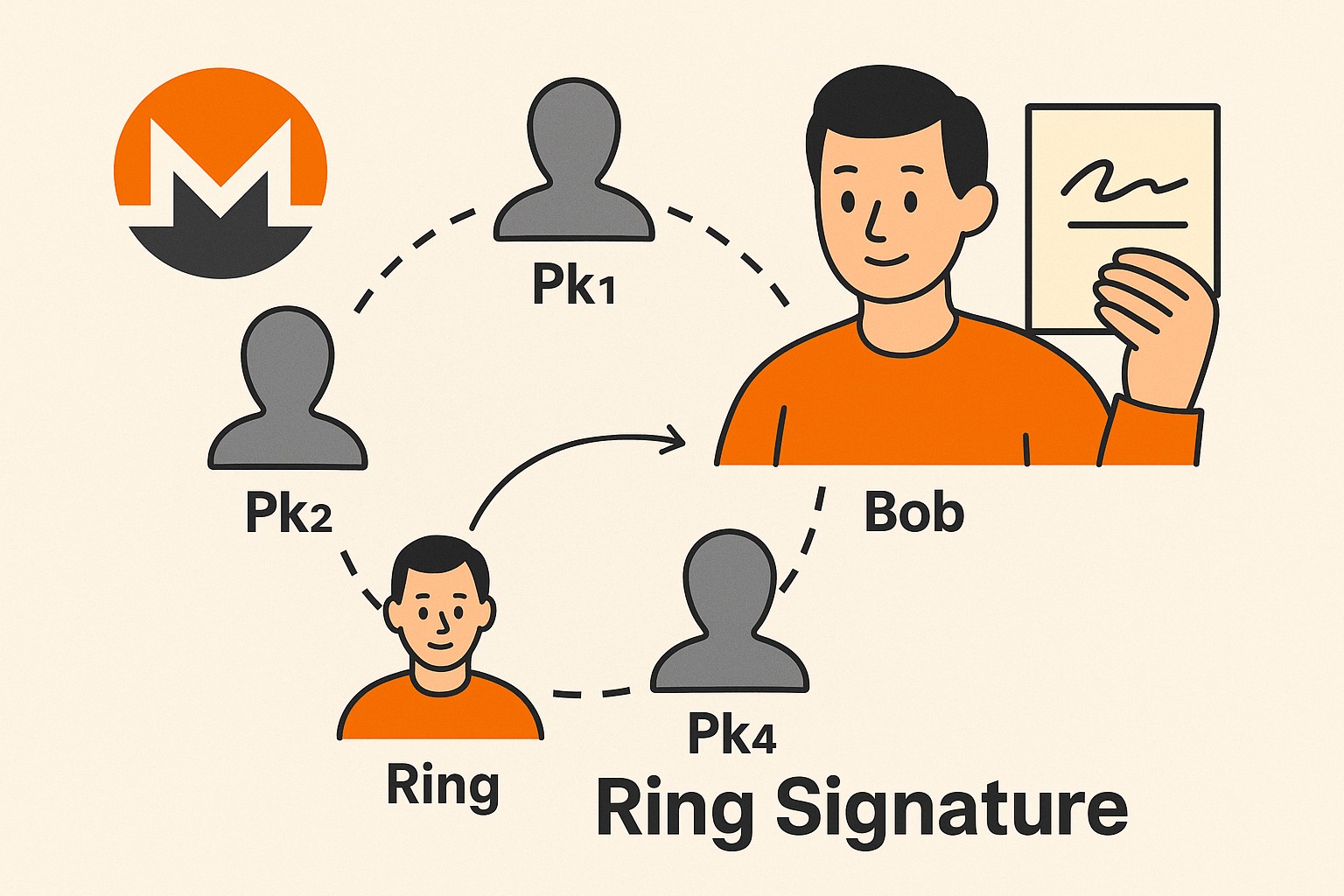
Introduction Ring Signatures Overview The main idea behind ring signatures is that a user $u$, who is part of a user group $$R =...