When we talk about self-custody and protecting our bitcoins, we understand that the seed used to generate our private keys must be completely isolated...
Bitcoin and cryptocurrencies in general use cryptography to ensure the ownership of coins, among many other aspects. The security is based on “hard” problems...
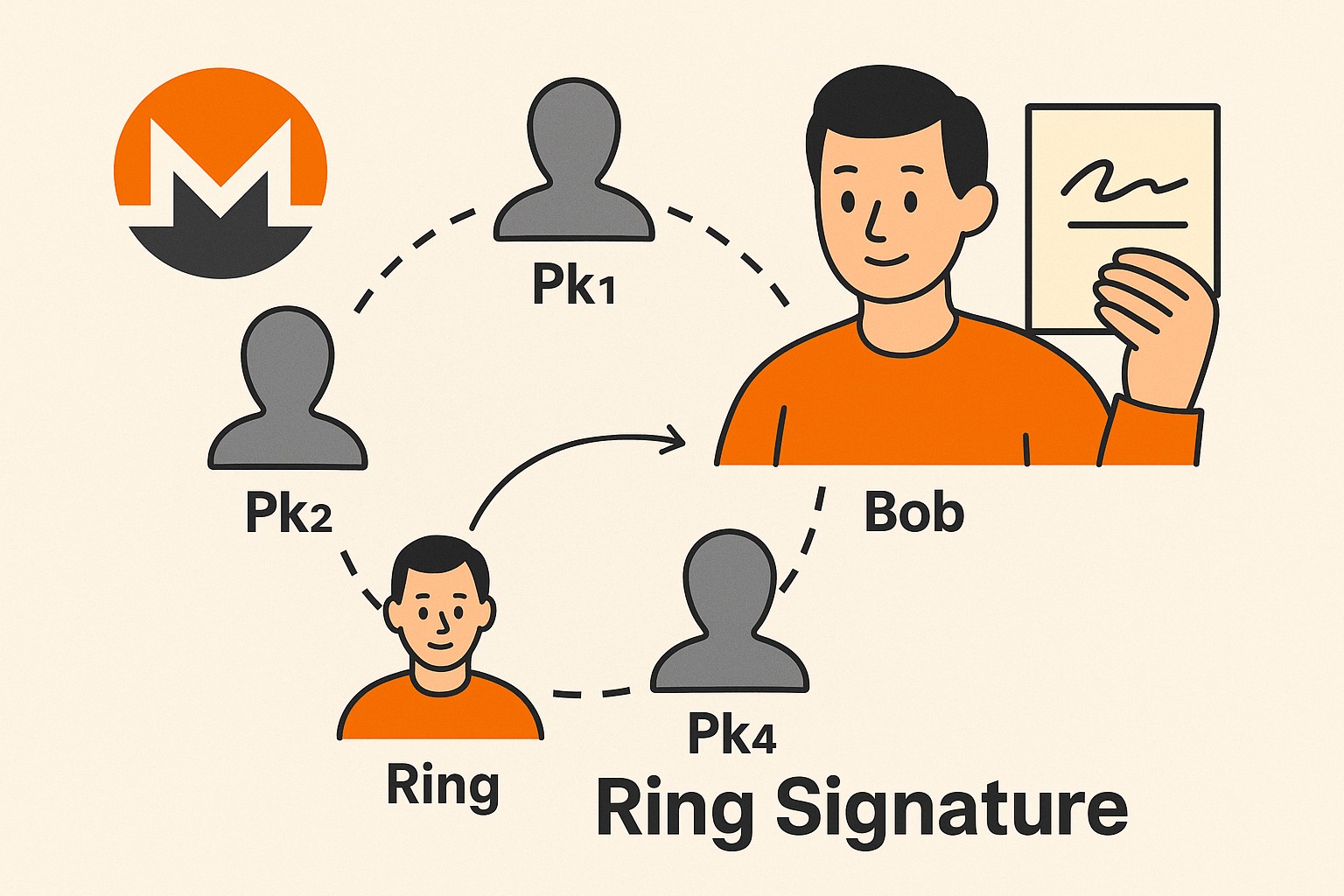
Introduction Ring Signatures Overview The main idea behind ring signatures is that a user $u$, who is part of a user group $$R =...
During my initial research period at UAB, I began developing a replica of the real Bitcoin mainnet. While this might sound unusual—especially given the...
📊 Bitcoin’s Decentralization: What the Data Really Says Bitcoin is intended to be a decentralized, trustless peer-to-peer currency. But how decentralized is the network, really, 15...
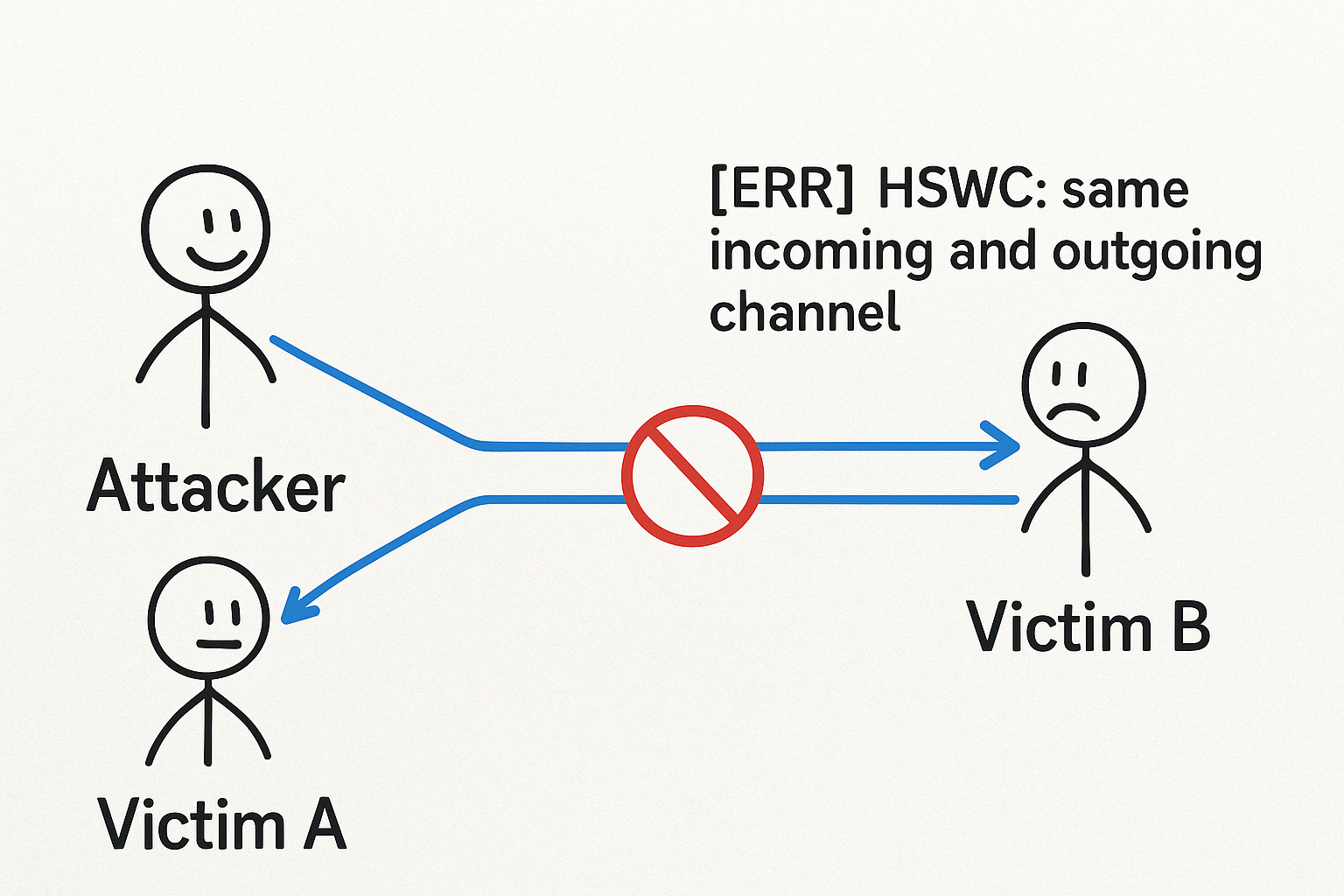
The Lightning Network (LN) is a dynamic and constantly evolving second-layer scaling solution for Bitcoin, designed to enable fast, low-cost transactions. Recently, the network...
By Ghazaleh Keshavarzkalhori, Cristina Perez-Sola, Guillermo Navarro-Arribas, Jordi Herrera-Joancomartí, and Habib Yajam In a world where data privacy is more important than ever, federated learning has...
We are currently conducting research on wallet fingerprinting in Bitcoin. In this work, we delve on the way that several Bitcoin wallets construct and...
Some time ago, we proposed a mechanism to address a long-standing issue in Bitcoin: the vulnerability of zero-confirmation (0-conf) transactions to double-spending attacks. Zero-confirmation...
We’ve recently submitted our latest paper to the 2025 7th International Conference on Blockchain Computing and Applications (BCCA), which will take place in Croatia. In...