Introduction
- Monero is a type of cryptocurrency, similar to Bitcoin. It was launched in April 2014 and, like many cryptocurrencies, is built on blockchain technology. This enables Monero to be decentralized, meaning no single person or organization has exclusive control over it.
- In both Monero and Bitcoin, all transaction records are stored publicly on their respective blockchains, making them visible to anyone. This transparency can lead to privacy concerns, as third parties can use blockchain analysis to trace and link transactions. Monero was specifically designed to address these privacy issues by offering complete anonymity for its users.
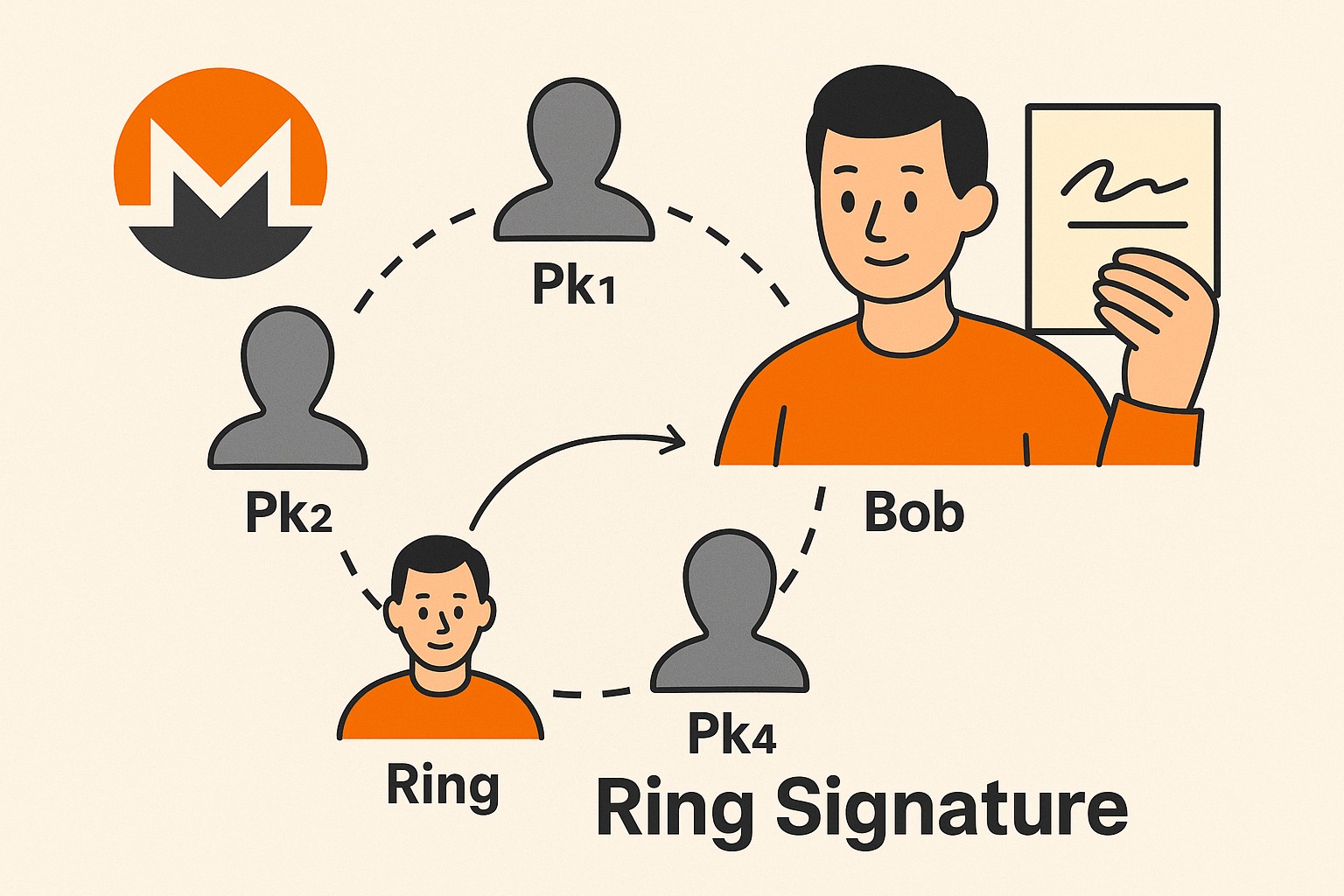
- Monero is built on the CryptoNote protocol, which introduced features like stealth addresses and ring signatures to keep both the sender’s and receiver’s identities anonymous. Today, we’ll focus on ring signatures and how they function in Monero.
Ring Signatures
Overview
The main idea behind ring signatures is that a user ![]() , who is part of a user group
, who is part of a user group
![]()
can sign a message ![]() such that anyone verifying the signature is assured that one of the members in
such that anyone verifying the signature is assured that one of the members in ![]() signed the message but cannot know which specific member it was.
signed the message but cannot know which specific member it was.
This protocol operates without the need for a trusted third party or the cooperation of all the users in the group. Each participant only needs a pair of private and public keys. Therefore, any user can choose the signers and generate the signature independently. This capability is especially useful when broadcasting information anonymously while still guaranteeing the integrity and origin of the message.
Key Pairs
Each group member holds a key pair:
![]()
When a member ![]() wishes to sign a message
wishes to sign a message ![]() , the signature generation process utilizes the private key
, the signature generation process utilizes the private key ![]() and the public keys of the other members
and the public keys of the other members ![]() . The resulting signature can be verified without disclosing the actual identity of the signer.
. The resulting signature can be verified without disclosing the actual identity of the signer.
The following example exposes in more detail how the ring signature is created and verified:
Example: Bob Creating a Ring Signature
Suppose Bob wants to create a ring signature. His steps are as follows:
- Calculate the System Key
Compute the key of the cryptosystem by hashing the message:![Rendered by QuickLaTeX.com \[k = h(m).\]](https://www.discrypt.cat/wp-content/ql-cache/quicklatex.com-7da3e0acaa89f2d9ecf79c67d529b257_l3.png)
- Determine the Parameter
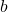
Choose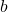 such that for every public key modulus
such that for every public key modulus 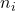 (with
(with 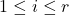 ) it holds that:
) it holds that:
![Rendered by QuickLaTeX.com \[2^b > n_i.\]](https://www.discrypt.cat/wp-content/ql-cache/quicklatex.com-4543dd8cea182977302d0a073759c821_l3.png)
(In RSA a public key is
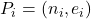 and a private key is
and a private key is  .)
.) - Generate Random Values
- Generate a random value
 of
of 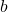 bits.
bits. - For each public key in the group except Bob’s, generate random
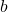 -bit values
-bit values 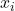 .
.
- Compute
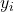 Values
Values
For each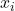 , compute:
, compute:
![Rendered by QuickLaTeX.com \[y_i = f_i(x_i).\]](https://www.discrypt.cat/wp-content/ql-cache/quicklatex.com-28d1864fdaeb07d6f83d53342f906a44_l3.png)
- Determine
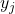 for Bob
for Bob
Bob calculates his corresponding value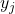 (where his key pair is
(where his key pair is 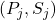 ) so that:
) so that:
![Rendered by QuickLaTeX.com \[C_{k,v}(y_1, y_2, \dots, y_r) = v.\]](https://www.discrypt.cat/wp-content/ql-cache/quicklatex.com-178368062f0081ad8c79f83196f7e8c7_l3.png)
C is a combination function that XORs values and encrypts the results with the key
, repeating until:
- Compute
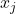
To avoid exposing his private key, Bob computes:![Rendered by QuickLaTeX.com \[x_j = f_j^{-1}(y_j),\]](https://www.discrypt.cat/wp-content/ql-cache/quicklatex.com-eaef281e3e1ddbe28fc16503c2114075_l3.png)
using his private key
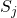 .
.
Final Ring Signature
![]()
Verification Process
- For each
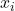 , compute:
, compute:
![Rendered by QuickLaTeX.com \[y_i = f_i(x_i).\]](https://www.discrypt.cat/wp-content/ql-cache/quicklatex.com-28d1864fdaeb07d6f83d53342f906a44_l3.png)
- Recompute the cryptosystem key:
![Rendered by QuickLaTeX.com \[k = h(m).\]](https://www.discrypt.cat/wp-content/ql-cache/quicklatex.com-7da3e0acaa89f2d9ecf79c67d529b257_l3.png)
- Check that
![Rendered by QuickLaTeX.com \[C_{k,v}(y_1, y_2, \dots, y_r) = v.\]](https://www.discrypt.cat/wp-content/ql-cache/quicklatex.com-178368062f0081ad8c79f83196f7e8c7_l3.png)
Ring Signatures in Monero Transactions
But how exactly do ring signatures help Monero improve privacy when making a transaction?
In Monero, when a user sends a transaction, they create a ring signature using their private key and a set of public keys from other unrelated users (called “decoys”), selected from previous blockchain outputs. To an outside observer, the transaction could have come from any member of the ring, making the real sender indistinguishable from the group.
For a ring size of ![]() , there are
, there are ![]() potential senders on the blockchain; only one is the actual spender, the rest are decoys. This breaks the link between transactions and their true origin, significantly enhancing privacy.
potential senders on the blockchain; only one is the actual spender, the rest are decoys. This breaks the link between transactions and their true origin, significantly enhancing privacy.
Final Thoughts
- While ring signatures greatly improve Monero’s privacy, they’re not perfect. Statistical and blockchain analysis can sometimes reveal the real input among decoys, especially if decoys aren’t uniformly chosen.
- The effectiveness depends on the anonymity set size. A ring size of 2 (1 real + 1 decoy) is far weaker than a ring size of 10 or more.
- Monero enforces a mandatory minimum ring size (currently 16) to ensure at least 15 decoys per transaction.
- Monero also uses Ring Confidential Transactions (RingCT) to hide amounts, combining ring signatures with Pedersen commitments so that transaction values remain confidential while ensuring no coins are created or destroyed.